Tuesday, October 22, 2013
Labels:
firewalls
,
malware
I was reading an interesting article over on LifeHacker attempting to make the case that outbound firewalls are worthless. For those that don't know what an outbound firewall does, its purpose is to block programs from making internet-bound connections without your approval. The Windows firewall presents something similar to the image below when this occurs:
Outbound Firewalls: Prevention is the Cure
Posted by
Aggregate Obscurity
at
12:28 AM
Are "Outbound Firewalls" worth it? (Short answer, yes)
I was reading an interesting article over on LifeHacker attempting to make the case that outbound firewalls are worthless. For those that don't know what an outbound firewall does, its purpose is to block programs from making internet-bound connections without your approval. The Windows firewall presents something similar to the image below when this occurs:
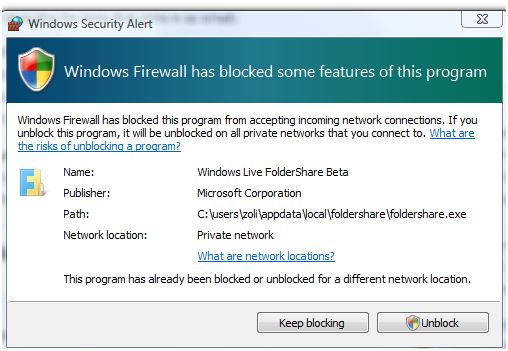 |
| Image Credit: zolierdos |
The main point of such operations, if you think about it from a perspective on trying to control malware, would be to block the malware from making a connection to the Internet without your knowledge. This assumes that you've already gone through the stage of visiting a compromised link, resulting in the installation of malware on your machine. Blocking malware at that stage is reactive, not proactive. See below for the associated illustration of this process:
Instead of waiting until that point, why not prevent it in the first place?
That's where prevention works in your favor. By preventing your browser from sending a request for that compromised or malicious link in the first place, you reduce the likelihood of infection.
Does that prevent you from getting infected from borrowing someone's malware-infested USB drive? Of course not. If you do have this prevention mechanism, and if you get infected from another vector such as the USB drive, then unless the prevention method is circumvented the malware will still get blocked when phoning home to its command and control servers. It's at this stage that the prevention mechanism would operate similar to a firewall blocking outbound Internet connections from untrusted programs.
Sold! Now what do I do?
There are many programs that performs this prevention aspect. Most "Internet Security Suites" from vendors such as McAfee, Kaspersky, and Trend Micro have web browser plug-ins that analyze each URL (website link) individually and will block known bad URLs. In my opinion though, to know that a link is bad requires one of two analyses:
1) Someone visited the link and became infected, at which point the vendor program detected the infection and reported the URL back to the vendor mothership for distribution to all other endpoints so those other endpoints are now protected.
2) A brand new malware link is established that no vendor has seen before. A vendor program installed for protection analyzes the content on this brand new link and dynamically assigns a threat analysis, blocking its access.
In this way, link analysis becomes very similar to virus detection. Look for the known bad (signatures), and identify the potentially bad (heuristics).
My favorite prevention software in this aspect is Blue Coat's K9 software. It's essentially a proxy agent that sits on your machine monitoring all outbound requests for content, and will block access to a site using both "signatures" and "heuristics" styles of link analysis. This isn't to say that other vendor programs don't have that capability, I've just had more familiarity with the K9 software.
If anyone would like me to post a complete review of K9, please let me know.
To be clear, I'm not advocating such URL analysis tools over outbound firewalls. I think they should be considered another layer of defense. Let them catch the majority of "bad" requests to prevent what they can, and still keep the outbound firewall active in case an unknown program is detected making an outbound connection attempt. Also note that these days many malware authors attempt to hide the outbound connection attempts through other means so these may not get detected by the outbound firewall, but it's still worth keeping around.
Subscribe to:
Post Comments
(
Atom
)








Nice article Matt. The graphics you used illustrate your explanation well.
ReplyDeleteThanks for sharing.